Digital Chain of Custody Done Right
Chain of custody has always been rife with “acceptable inefficiencies”—a polite industry term for blind spots between verification points where assets effectively disappear from secure oversight.
Companies have had to tolerate this reality for decades—these gaps between checkpoints where custody becomes a matter of faith rather than fact. These “blind spots” typically emerge during transport phases and handling intervals. All documented perfectly on either end. All completely unverified in between.
For a time, these vulnerabilities were unavoidable due to technological limitations, resource constraints and the physical challenges associated with continuous verification. The industry’s response? Tighten the checkpoints. Document more thoroughly. Hope more intensely.
Today, those constraints no longer exist.
The convergence of automated forensic profiling for devices, GPS/cellular tracking, parent-child architecture, cross-boundary digital handshakes and human security protocols has eliminated the need to tolerate “acceptable risk.” What the industry considered impossible is now, in the hands of some, an operational reality.
A new approach to chain of custody has emerged—one that’s completely digital, always-on, with gapless oversight and granular control. One that doesn’t stifle efficiency in the name of security but streamlines it through real-time verification. And one that eliminates blind spots rather than merely documents their boundaries.
We call this precision security paradigm Continuous Custody Intelligence.
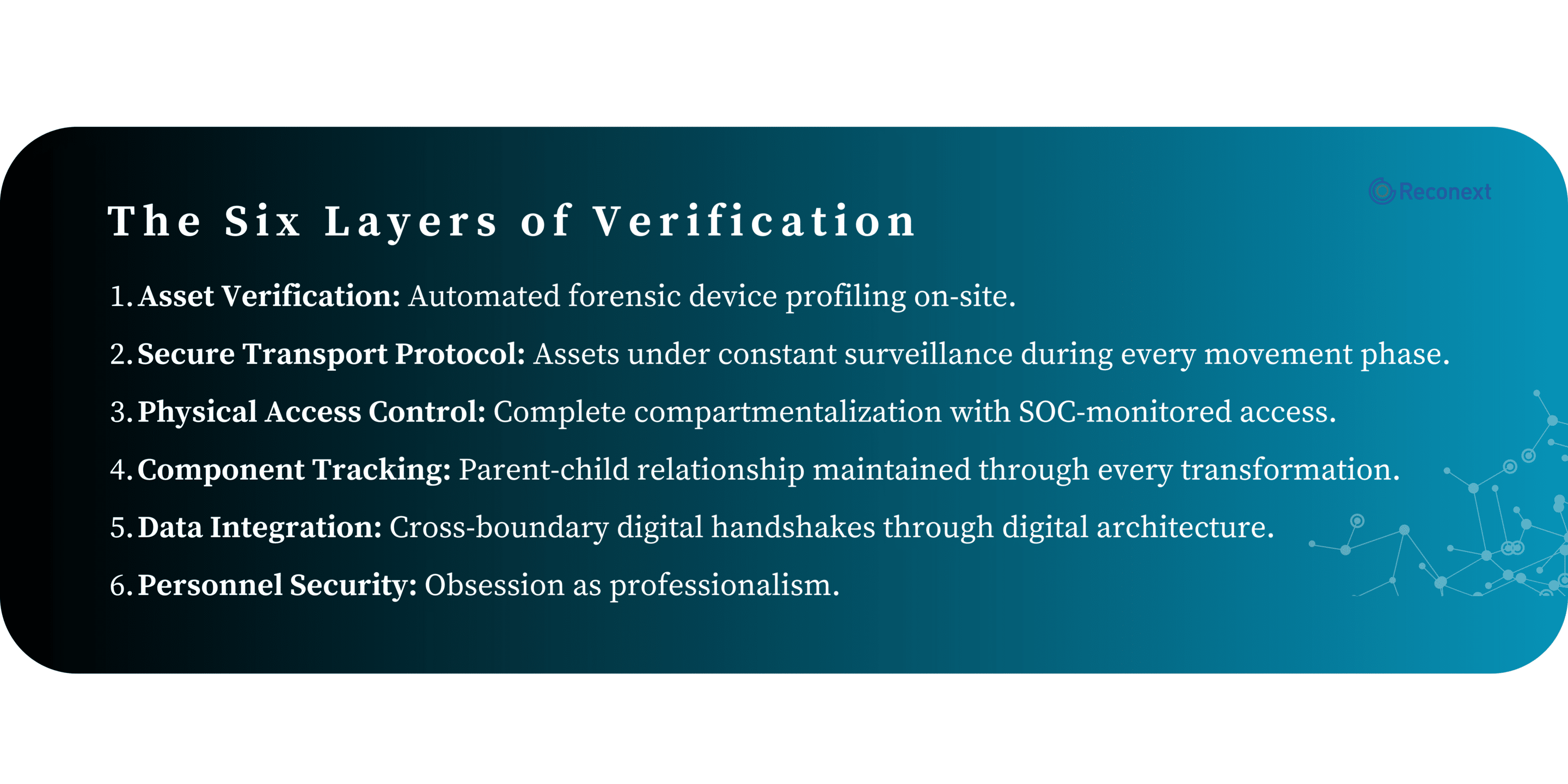
Today, we’ll show you how this modern approach to chain of custody works through the six layers of verification. Let’s dive in.
LAYER 1 | ASSET VERIFICATION
Visual confirmation represents the weakest form of verification—the security equivalent of “looks about right.” Genuine security demands complete device mapping against expected configurations.
The Continuous Custody Intelligence (CCI) approach begins before assets even leave your facility. Specialized hardware verification tools connect directly to your equipment, generating complete digital profiles of every device. These systems identify serial numbers, validate hardware configurations and cross-reference component-level details against manufacturer BOMs and expected specifications.
This on-site verification becomes the foundation for all subsequent custody validation. When these assets arrive at a processing facility, they undergo the same automated profiling process, creating an exact match verification that confirms nothing changed in transit.
When hardware or software don’t match expectations, the Material Review Board quarantines anomalies immediately. Everything stops until verification completes.
Take this example: If a manifest claims 12 drives of a specific model arrived, but verification identifies 11 of that model plus one variant, this discrepancy triggers immediate resolution protocols. Not during month-end reconciliation. Within minutes.
Visual documentation is equally thorough. During disassembly, every significant component—drives, memory modules, boards—is photographed and directly linked to its digital tracking record.
This documentation doesn’t exist to satisfy auditors. We’re not playing the same game. While others prepare for audits, we’ve designed systems that make standard auditing frameworks feel like measuring a tsunami with a ruler.
Put it this way: we don’t prepare for audits. Audits prepare for us.
When verification fails, the hard-stop protocol isn’t a policy recommendation. It’s a system architecture reality. The process physically cannot proceed until verification completes successfully. Policy can be ignored. System architecture cannot.
Once verified at the source, assets must move.
LAYER 2 | SECURE TRANSPORT PROTOCOL
The moment assets leave your controlled environment, conventional security begins its rapid deterioration. The truck pulls away, and suddenly the integrity of your chain of custody becomes a dice roll.
This moment is precisely where most security architectures fail.
Continuous Custody Intelligence transforms transportation from a security vulnerability into the first layer of comprehensive protection. This approach to transit security recognizes that transportation isn’t a logistics function with security bolted on. It’s a security operation that happens to involve movement.
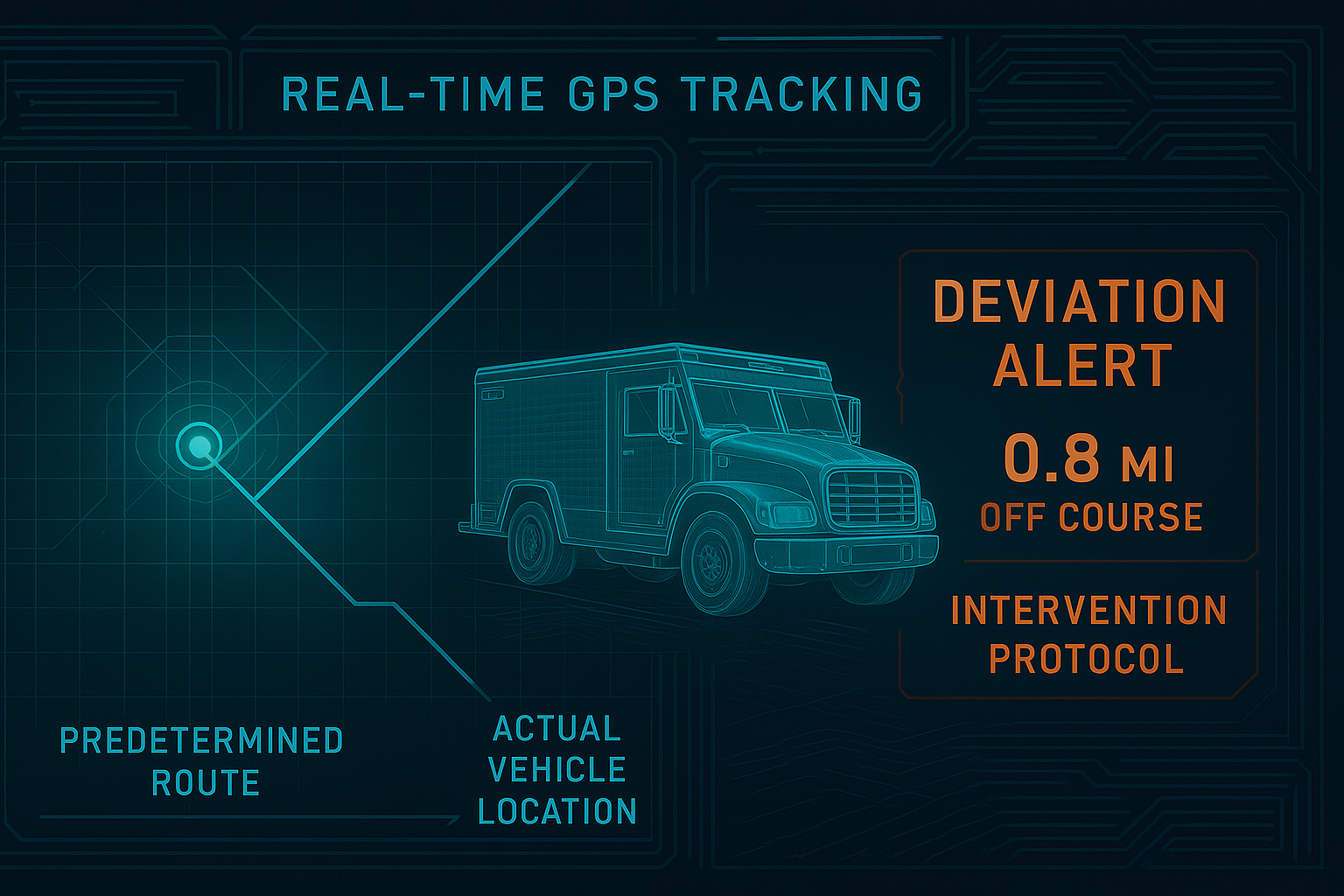
GPS and cellular tracking don’t just passively record position. They enable real-time intervention. RFID systems constantly monitor the truck’s progress. A driver approaching the wrong building triggers corrective action before they even park.
(Most providers will tell you they track shipments. Ask them what happens when a driver goes 0.8 miles off route. Watch them blink.)
For organizations serious about security, asset-based carriers become the only acceptable option. Never brokers. Never subcontractors. Every driver undergoes comprehensive vetting. Every route is predetermined. Every deviation triggers immediate response protocols.
For high-value shipments, armed security personnel—usually off-duty law enforcement professionals—maintain continuous visual contact. The assets never leave their sight. Not for a moment and not for any reason.
And if the impossible happens? If all these safeguards somehow fail? Remote shutdown capabilities can render stolen assets worthless. They become expensive paperweights without the digital keys only the right people possess.
This isn’t paranoia. It’s the baseline for modern security. It’s the minimum acceptable standard when failure means catastrophic data exposure. And honestly, once you see what happens when Continuous Custody Intelligence is implemented correctly, you’ll wonder why everyone doesn’t do it this way.
LAYER 3 | PHYSICAL ACCESS CONTROL
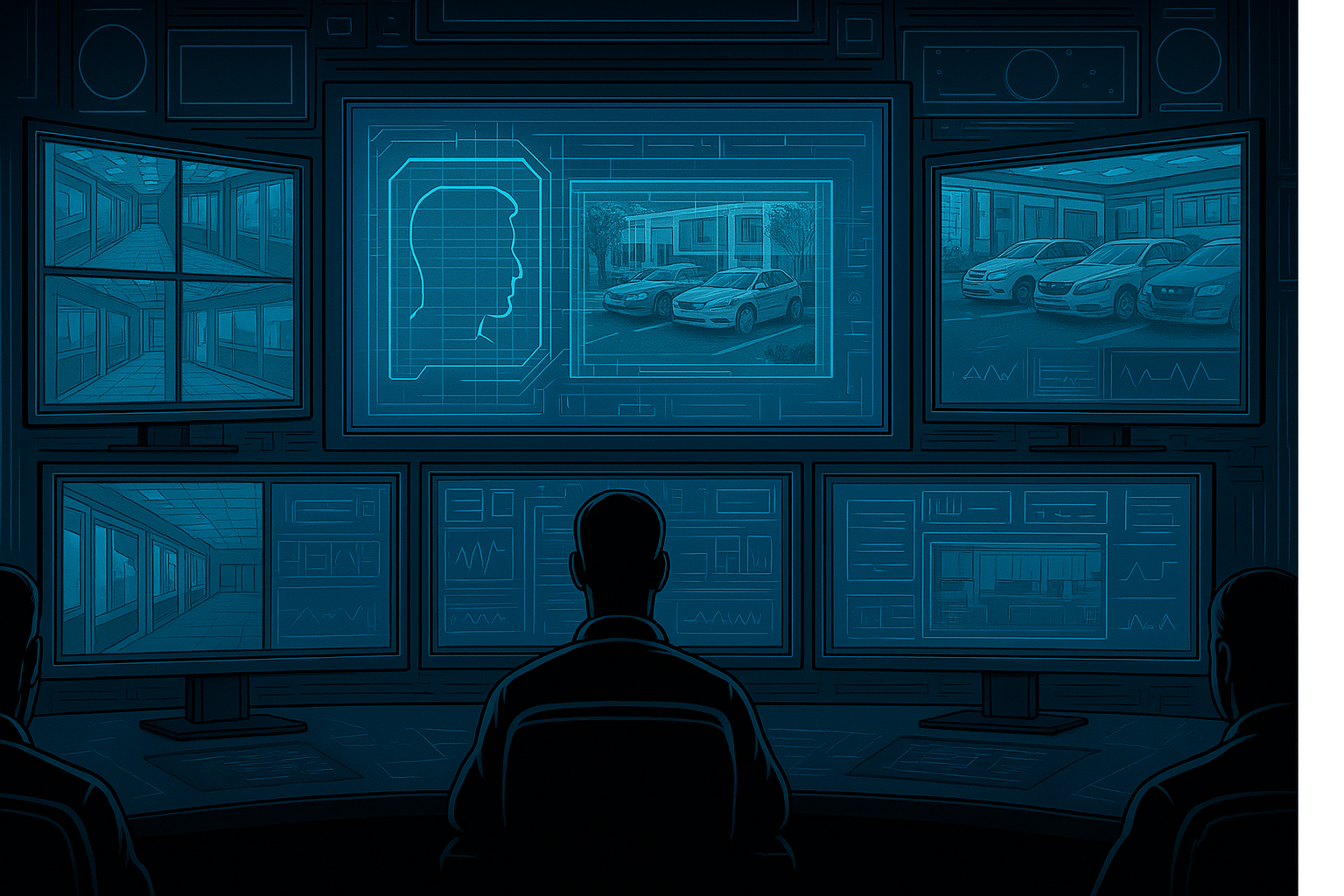
A genuinely secure facility looks nothing like what most clients imagine. It’s not badges and cameras and men in uniforms. It’s a Security Operations Center staffed by personnel with criminal justice backgrounds analyzing behavior patterns in real-time.
These professionals aren’t watching for obvious theft. They’re searching for the subtle behavioral anomalies that precede security breaches. They’re studying movement patterns, timing discrepancies and micro-expressions that most security personnel would miss entirely.
Hundreds of cameras with AI-enhanced motion detection create continuous surveillance. Every entrance, exit and secure area requires multi-factor approval. No single person can access sensitive areas alone. The SOC verifies identity. A supervisor authorizes access. The entire operation remains under constant monitoring.
(The average security camera exists to document what went wrong. The right security camera, with AI-enhanced motion detection and real-time behavioral analysis, exists to prevent it from happening in the first place.)
This level of control rewires security psychology without impeding productivity. When employees can physically see these boundaries, unauthorized access doesn’t happen by mistake––or at all. And legitimate work continues to flow uninterrupted. The system doesn’t issue blanket denials; it grants precise permissions. It says ‘yes’ to exactly the right things, enhancing both security and efficiency simultaneously. This precise control is a hallmark of the Continuous Custody Intelligence methodology.
LAYER 4 | COMPONENT TRACKING
Device disassembly: where chain of custody is the weakest link.
When assets transform from unified devices to individual components, conventional tracking systems typically resort to compromises. That single laptop with one tracking number suddenly becomes a motherboard, hard drive, memory modules, display and peripherals—multiplying tracking complexity exponentially.
Most systems respond by tracking only major components. The rest disappear into aggregate counts. Precision gives way to approximation, creating the perfect environment for loss, theft and compliance violations.
The solution? Parent-child relationship architecture that captures each component’s entire journey. When a server enters the system, each component inherits the custody chain. Removed hard drives maintain documentation linking them to the original asset. Harvested memory modules retain their provenance data.
This granular approach doesn’t just satisfy compliance requirements. It enables both security AND sustainability—the ability to reuse components without sacrificing verification. Parts harvesting occurs while maintaining complete chain of custody, down to individual memory modules.
For data-containing devices, this tracking offers key documentation. Case in point: certificates of destruction or erasure can be generated for specific components rather than just the parent device—creating the verification that compliance requires and executives demand.
The next challenge: making all these systems talk to each other.
LAYER 5 | DATA INTEGRATION
The Achilles’ heel of security: systems that don’t talk to each other.
Data integration is the backbone of Continuous Custody Intelligence. It transforms periodic reports into real-time verification. Cross-boundary data flows securely through multiple protocols. Each transaction captures reality—who did what and when—not just intentions.
This kind of real-time verification demands two critical safeguards. First, absolute data separation between clients. The architecture builds this directly into the database layer through program IDs, creating structural barriers rather than policy-based ones. Competitors cannot access each other’s asset information because the system makes it physically impossible.
Second, the system requires verification before progress. Required data fields prevent advancement without confirmation. If a component can’t be tracked, there’s no override option or temporary workaround. The system enforces a dead stop until verification completes. Not “here’s a warning” or “let’s flag this for review later.”
This creates an obvious challenge: rigid verification could paralyze operations. The elegance of this stratified approach is how it balances absolute security with operational velocity. Updates occur in real-time—measured in minutes, not days. It finds problems AND enables right-sized action at operational speed—intervening only where intervention is actually needed, not where it might be needed.
Perfect system integration is impressive. But what’s more impressive is when it survives contact with the people who use it daily.
LAYER 6 | PERSONNEL SECURITY
Technology has limits. Humans have vulnerabilities. A complete security architecture addresses both.
(Most breaches don’t come from malicious intent. They come from people who didn’t recognize a security situation until it was too late.)
Addressing the human element starts with recognizing that technical skills and clean background checks aren’t enough. Our personnel selection goes beyond standard screening to identify security mindsets––people who instinctively recognize vulnerabilities others miss. The vetting process examines behavioral patterns, not just employment history.
New team members undergo a “baby steps” protocol in controlled environments. Security scenarios are deliberately created to test responses: “We set up a shipment that looks like it just went awry. Did you catch that? How did that happen?” This reveals how people respond when systems don’t work as expected.
In security contexts, “control freak” isn’t a personality flaw—it’s a compliment. The distinction that matters: control isn’t about locking everything down. It’s about immediate awareness enabling right-sized action:knowing exactly what’s happening, when it’s happening, so responses can be precisely calibrated to the actual threat.
THE REALITY BEYOND THEORY
Continuous Custody Intelligence is not an evolution of traditional chain of custody—it’s a fundamental shift to a more connected, always-on, gapless way to secure chain of custody. And it’s already protecting billions in assets at Reconext facilities worldwide.
Companies implementing our approach experience fundamental transformations in their security posture. Not incremental improvements, but comprehensive restructuring of what security means in practice. The blind spots that conventional approaches accept as “acceptable inefficiencies” disappear entirely. Verification becomes continuous rather than periodic. Hope ceases to be a factor in the security equation.
These aren’t theoretical benefits.
A global technology leader with a commercially viable virtual reality product approached us with extreme security requirements: blanked-out areas, isolated networks, custom camera systems, even secured disposal of cardboard packaging.
The revealing moment came when a representative from another division of this same company toured our facility. They noticed a segregated area they couldn’t access and asked about it. Their reaction upon discovering it was their own company’s processing area? Genuine shock. They had no idea Reconext was already handling their sensitive assets from another division.
“You guys have surpassed the security of our company to the extent where you have this,” was their immediate response. The compartmentalization was so complete that different divisions of the same company couldn’t see each other’s operations.
The result? A clean consolidation of all ITAD operations under Reconext management. Not because of marketing or sales pitches. Because they recognized the fundamental difference between security theater and actual security.
In security, there is no “good enough.” There is only “completely secure” or “vulnerable.”
The choice isn’t just obvious. It’s inevitable.
_______________________________________________________________________________________________________________________
This approach has transformed security operations for organizations across industries. If you’re curious about what it might look like in your environment, our experts at Reconext would be happy to discuss it. Contact us!